Unveiling the Power of Norse Map Attacks: A Comprehensive Guide
Related Articles: Unveiling the Power of Norse Map Attacks: A Comprehensive Guide
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unveiling the Power of Norse Map Attacks: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Power of Norse Map Attacks: A Comprehensive Guide

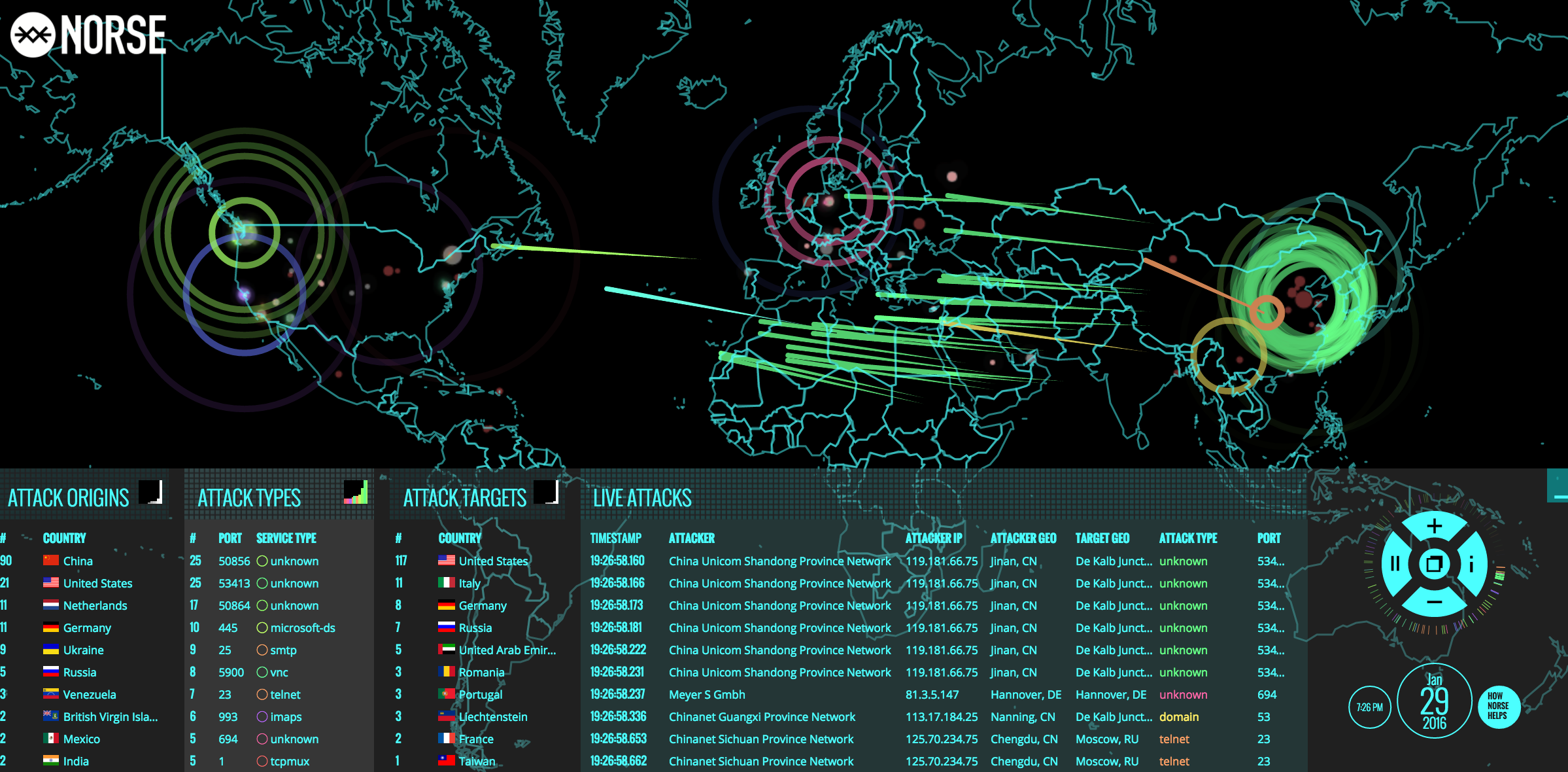
The realm of cybersecurity is constantly evolving, with adversaries employing increasingly sophisticated tactics to infiltrate systems and exploit vulnerabilities. One such attack, often referred to as a "Norse Map" attack, has garnered attention for its unique approach to exploiting network infrastructure. This article delves into the intricacies of this attack vector, exploring its mechanics, potential impact, and strategies for mitigation.
Understanding the Norse Map Attack:
The term "Norse Map" is a descriptive moniker, highlighting the attack’s reliance on mapping and exploiting network topology. This attack leverages the inherent vulnerabilities of network infrastructure, particularly those related to routing protocols and network segmentation.
Key Components of a Norse Map Attack:
-
Network Reconnaissance: The attacker begins by gathering information about the target network. This includes identifying critical network devices, mapping network segments, and understanding routing protocols. This phase often involves employing reconnaissance tools, scanning for open ports, and analyzing network traffic.
-
Exploiting Network Segmentation: Once the attacker has a comprehensive understanding of the network’s structure, they focus on exploiting network segmentation vulnerabilities. This involves identifying and leveraging misconfigurations, weak access controls, or poorly implemented network segmentation policies. The goal is to traverse network boundaries and gain access to sensitive resources.
-
Lateral Movement: The attacker utilizes compromised devices as stepping stones to move laterally within the network. This involves leveraging vulnerabilities in network protocols, exploiting shared credentials, or utilizing tools like PowerShell Empire to gain access to other systems.
-
Data Exfiltration: The ultimate objective is to steal sensitive data. The attacker may use various methods for exfiltration, including transferring data through compromised devices, using covert channels, or exploiting network vulnerabilities to establish backdoors.
Illustrative Scenarios:
- Compromising a Network Segment: An attacker could exploit a misconfigured firewall rule that allows unauthorized access to a specific network segment. This could grant them access to critical servers, databases, or other sensitive resources.
- Leveraging VPN Tunnels: The attacker might exploit vulnerabilities in VPN configurations to gain access to the target network. This could allow them to bypass security measures and access sensitive data without detection.
- Exploiting Routing Protocols: The attacker could manipulate routing protocols, such as BGP, to redirect network traffic to their controlled systems. This could lead to data interception, denial-of-service attacks, or other malicious activities.
Impact of Norse Map Attacks:
Norse Map attacks can have significant consequences for organizations. They can lead to:
- Data Breaches: The theft of sensitive information, including financial data, customer records, intellectual property, and confidential documents.
- Disruption of Operations: The compromise of critical systems and services can lead to downtime, service outages, and operational disruptions.
- Financial Loss: The cost of data breaches, remediation efforts, and reputational damage can be substantial.
- Regulatory Compliance Issues: Data breaches can trigger regulatory investigations and penalties, particularly in industries with strict data privacy regulations.
Mitigating Norse Map Attacks:
Organizations can effectively mitigate the risks associated with Norse Map attacks by implementing a comprehensive security strategy that includes:
- Network Segmentation: Implementing strong network segmentation policies to restrict access to sensitive resources and prevent lateral movement.
- Regular Security Audits: Conducting regular security audits to identify and address network vulnerabilities, misconfigurations, and weak access controls.
- Secure Network Devices: Ensuring that all network devices are updated with the latest security patches and configurations.
- Multi-Factor Authentication: Implementing multi-factor authentication for all network access points to enhance security and prevent unauthorized access.
- Intrusion Detection and Prevention Systems (IDS/IPS): Deploying IDS/IPS solutions to detect and prevent malicious activities on the network.
- Security Awareness Training: Educating employees about security best practices, phishing scams, and social engineering techniques to reduce the risk of human error.
Frequently Asked Questions (FAQs) about Norse Map Attacks:
Q: How can I identify if my network is being targeted by a Norse Map attack?
A: Identifying a Norse Map attack can be challenging as attackers often employ stealthy techniques. However, some indicators include:
- Unusual network traffic patterns: Observe spikes in network traffic, particularly to or from unknown IP addresses.
- Suspicious login attempts: Monitor for unusual login attempts from unfamiliar locations or devices.
- Changes in network configuration: Monitor for unauthorized changes to network configurations, firewall rules, or routing protocols.
- Unexpected device behavior: Observe any unexpected behavior from network devices, such as high CPU utilization or unusual network activity.
Q: What are the best practices for securing my network against Norse Map attacks?
A: The best practices for securing your network against Norse Map attacks include:
- Implementing strong network segmentation: Divide your network into smaller, isolated segments to limit the impact of a compromise.
- Regularly patching and updating network devices: Ensure that all network devices are running the latest security patches and configurations.
- Implementing robust access controls: Restrict access to sensitive resources and enforce strong password policies.
- Monitoring network traffic and activity: Use network monitoring tools to detect suspicious activity and potential intrusions.
- Conducting regular security audits: Periodically assess your network security posture to identify and address vulnerabilities.
Q: What are the key differences between a Norse Map attack and other network attacks?
A: Norse Map attacks differ from other network attacks in their emphasis on exploiting network topology and segmentation vulnerabilities. While other attacks might focus on exploiting specific vulnerabilities in software or operating systems, Norse Map attacks leverage the inherent weaknesses of network infrastructure to gain access to sensitive resources.
Conclusion:
Norse Map attacks represent a significant threat to organizations, leveraging network infrastructure vulnerabilities to gain unauthorized access and steal sensitive data. Understanding the mechanics of these attacks, implementing robust security measures, and maintaining a proactive security posture are crucial for mitigating the risks associated with Norse Map attacks. By embracing a comprehensive approach to cybersecurity, organizations can effectively protect their networks and data from the evolving threats posed by sophisticated adversaries.






Closure
Thus, we hope this article has provided valuable insights into Unveiling the Power of Norse Map Attacks: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!
