The Norris Attack Map: A Visual Tool for Network Security
Related Articles: The Norris Attack Map: A Visual Tool for Network Security
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to The Norris Attack Map: A Visual Tool for Network Security. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Norris Attack Map: A Visual Tool for Network Security

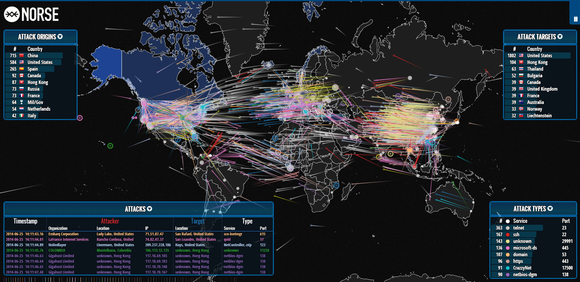
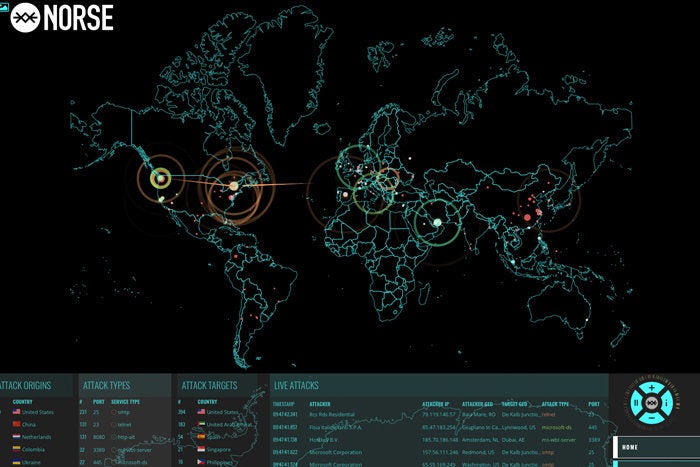
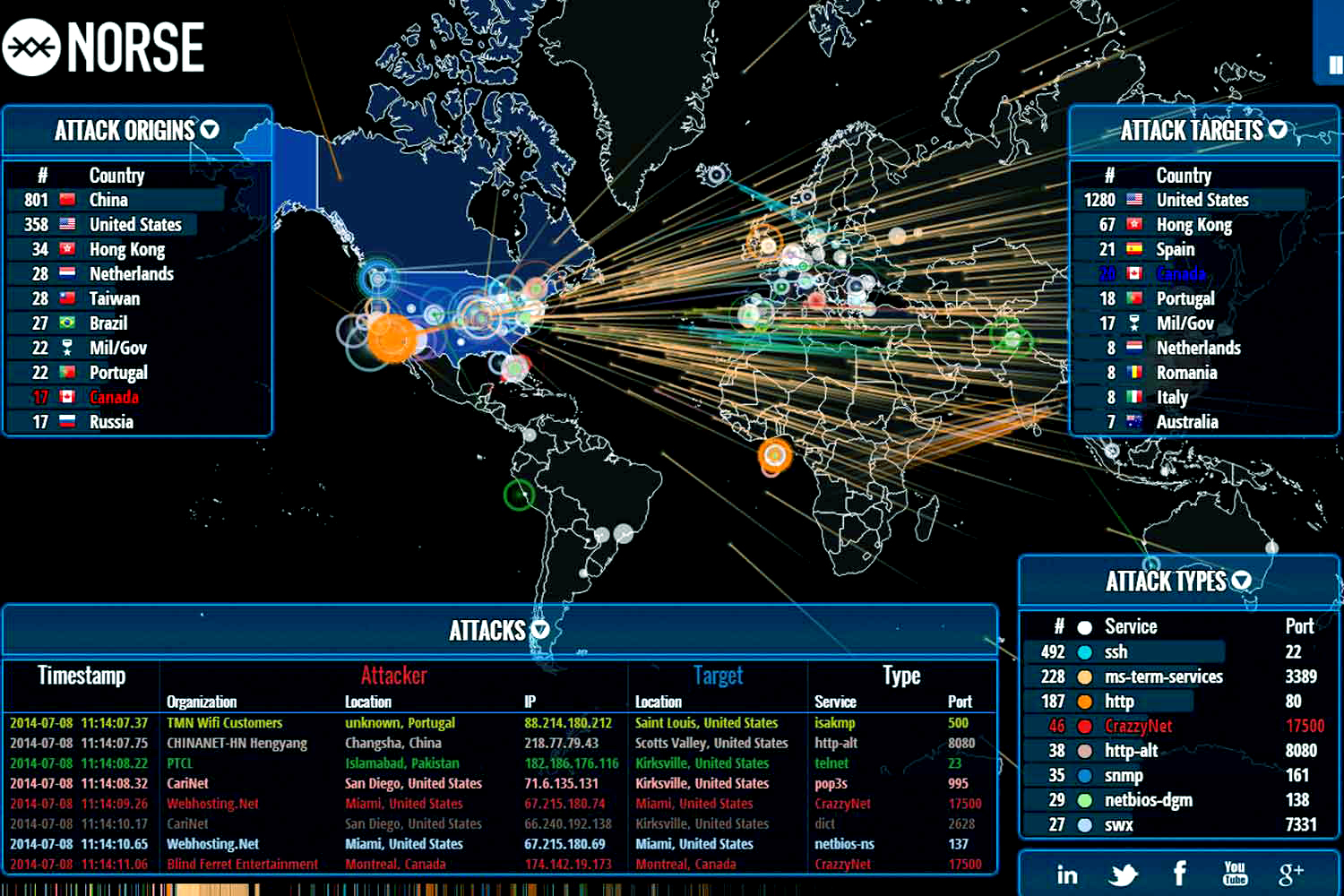
The Norris Attack Map, a visual representation of potential attack vectors and attack surfaces within a network, serves as a crucial tool for cybersecurity professionals. This map, developed by security researcher and consultant, Chris Norris, offers a comprehensive understanding of an organization’s vulnerabilities, helping to prioritize mitigation efforts and enhance overall security posture.
Understanding the Norris Attack Map
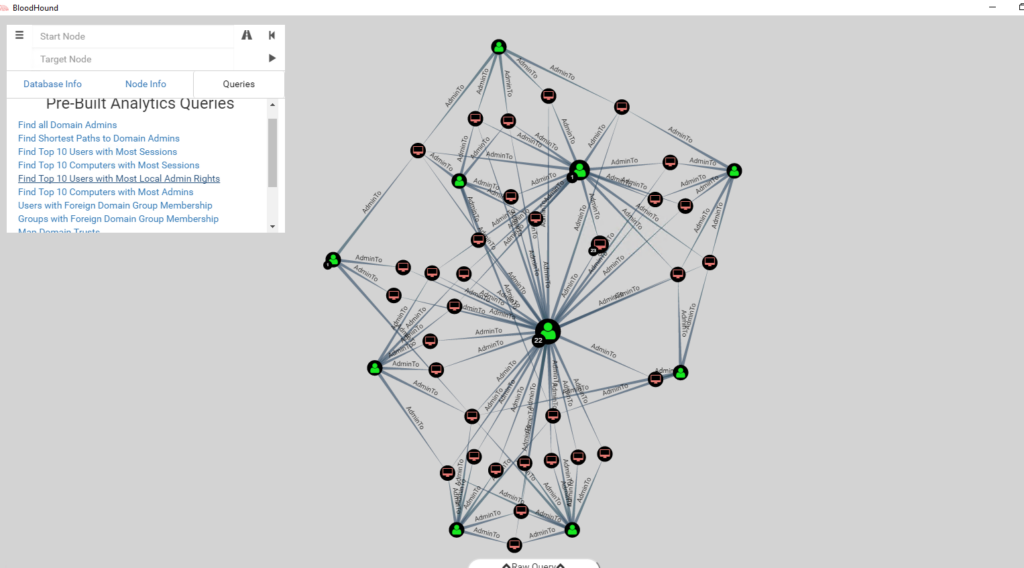
The Norris Attack Map is a visual representation of an organization’s network infrastructure, encompassing all connected devices, services, and applications. It utilizes a tree-like structure, with the root representing the organization’s core network and branches extending to individual systems and services. Each node on the map represents a potential entry point for attackers, highlighting the associated vulnerabilities and potential attack vectors.
Key Components of the Norris Attack Map
The map comprises several key components, each playing a critical role in understanding an organization’s security landscape:
- Attack Surface: The attack surface represents all potential entry points for attackers, including exposed services, applications, and devices. This includes web servers, databases, network devices, and even user endpoints.
- Vulnerabilities: Each node on the map lists known vulnerabilities associated with the respective system or service. This includes common vulnerabilities and exploits (CVEs), misconfigurations, and outdated software versions.
- Attack Vectors: The map outlines various attack vectors that attackers could utilize to exploit vulnerabilities. These include common techniques like SQL injection, cross-site scripting (XSS), brute-force attacks, and denial-of-service (DoS) attacks.
- Mitigations: The map provides recommendations for mitigating identified vulnerabilities, including patching, hardening configurations, implementing security controls, and deploying security software.
Benefits of Using the Norris Attack Map
The Norris Attack Map offers several benefits for organizations seeking to improve their cybersecurity posture:
- Comprehensive Vulnerability Assessment: The map facilitates a comprehensive assessment of an organization’s attack surface, identifying all potential entry points for attackers.
- Prioritized Mitigation Efforts: The map helps prioritize mitigation efforts by highlighting the most critical vulnerabilities and attack vectors. This allows organizations to focus on the most pressing security risks first.
- Improved Communication: The map provides a visual representation of security risks, facilitating communication between security teams, management, and other stakeholders.
- Enhanced Security Awareness: The map can be used to raise awareness about cybersecurity threats and vulnerabilities among employees, fostering a culture of security within the organization.
- Continuous Improvement: The map is a dynamic tool that can be updated regularly to reflect changes in the organization’s network infrastructure, security vulnerabilities, and emerging threats.
Creating a Norris Attack Map
Building a Norris Attack Map requires a systematic approach, involving the following steps:
- Inventory Network Assets: Identify all connected devices, services, and applications within the organization’s network.
- Map Network Topology: Create a visual representation of the network’s physical and logical structure, including connections between devices and services.
- Identify Vulnerabilities: Perform vulnerability scans and assessments to identify known vulnerabilities associated with each system and service.
- Define Attack Vectors: Identify potential attack vectors that attackers could exploit to compromise the organization’s network.
- Develop Mitigation Strategies: Develop mitigation strategies for each identified vulnerability and attack vector, including patching, hardening, and implementing security controls.
- Document and Update: Document the map and its associated information, and regularly update it to reflect changes in the organization’s network infrastructure, security vulnerabilities, and emerging threats.
FAQs about the Norris Attack Map
1. What is the difference between a Norris Attack Map and a traditional vulnerability scan?
While both methods aim to identify vulnerabilities, a traditional vulnerability scan focuses on identifying known vulnerabilities within a system or service. The Norris Attack Map goes beyond this by mapping the entire network infrastructure, considering the interconnectedness of systems and services, and identifying potential attack vectors.
2. How often should the Norris Attack Map be updated?
The map should be updated regularly, at least quarterly, to reflect changes in the organization’s network infrastructure, security vulnerabilities, and emerging threats.
3. Can the Norris Attack Map be used for organizations of all sizes?
Yes, the Norris Attack Map can be used by organizations of all sizes, from small businesses to large enterprises. The complexity of the map can be adjusted to suit the specific needs of the organization.
4. What tools can be used to create a Norris Attack Map?
There are various tools available to create a Norris Attack Map, including network mapping tools, vulnerability scanning software, and security information and event management (SIEM) systems.
Tips for Using the Norris Attack Map
- Involve Security Professionals: Involve experienced security professionals in the creation and maintenance of the map to ensure accuracy and completeness.
- Use Standardized Terminology: Use standardized terminology and conventions to facilitate communication and understanding across the organization.
- Prioritize Mitigation Efforts: Prioritize mitigation efforts based on the severity of vulnerabilities and the likelihood of attack.
- Regularly Review and Update: Regularly review and update the map to reflect changes in the organization’s network infrastructure, security vulnerabilities, and emerging threats.
Conclusion
The Norris Attack Map provides a comprehensive and visually intuitive approach to understanding an organization’s security posture. By mapping the network infrastructure, identifying vulnerabilities, and outlining potential attack vectors, the map empowers organizations to prioritize mitigation efforts, enhance security awareness, and strengthen their overall cybersecurity defenses. Implementing and maintaining a Norris Attack Map is a critical step for organizations seeking to proactively protect their assets and data from cyber threats.



Closure
Thus, we hope this article has provided valuable insights into The Norris Attack Map: A Visual Tool for Network Security. We thank you for taking the time to read this article. See you in our next article!