Navigating the Landscape of Innovation: A Comprehensive Guide to the ISA Framework
Related Articles: Navigating the Landscape of Innovation: A Comprehensive Guide to the ISA Framework
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Landscape of Innovation: A Comprehensive Guide to the ISA Framework. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Landscape of Innovation: A Comprehensive Guide to the ISA Framework

The world of technology is in constant flux, with new innovations emerging at an unprecedented pace. This rapid evolution necessitates a framework that can guide the development and deployment of these advancements, ensuring they are both beneficial and responsible. Enter the International Standards Organization (ISO), a global organization dedicated to developing and promoting international standards. One of its key initiatives, the International Standard for Information Security (ISO/IEC 27001), commonly referred to as ISO 27001, stands as a cornerstone for safeguarding information assets within organizations.
Understanding the Map of ISO 27001: A Framework for Information Security Management
ISO 27001 is not a static document; it is a dynamic framework encompassing a comprehensive set of guidelines and best practices for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). This framework serves as a roadmap for organizations to effectively manage their information security risks, ensuring the confidentiality, integrity, and availability of their sensitive data.
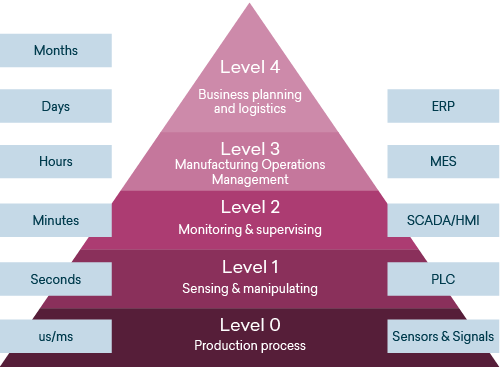
The framework’s structure is best visualized as a map, with each component representing a crucial element in the overall security landscape. This map is divided into 14 key domains, each addressing a specific aspect of information security:
- Security Policy: Defines the organization’s commitment to information security and sets the foundation for all subsequent security measures.
- Organizational Security: Addresses the organizational structure, responsibilities, and processes related to information security.
- Asset Management: Identifies and categorizes information assets, assessing their value and potential risks.
- Human Resource Security: Focuses on managing human risks, such as employee negligence, insider threats, and social engineering.
- Physical and Environmental Security: Addresses the protection of physical assets, such as data centers, servers, and network infrastructure.
- Communication and Operations Management: Ensures secure communication channels and processes, including data transmission, storage, and processing.
- Access Control: Establishes and enforces access controls to restrict unauthorized access to information assets.
- System Acquisition, Development, and Maintenance: Covers the secure development and maintenance of systems and applications.
- Information Security Incident Management: Defines procedures for handling security incidents, including detection, response, and recovery.
- Business Continuity Management: Ensures the organization’s ability to maintain critical business operations in the face of disruptions.
- Compliance: Addresses legal and regulatory requirements related to information security.
- Information Security Risk Assessment: Identifies, analyzes, and evaluates information security risks.
- Information Security Risk Treatment: Develops and implements controls to mitigate identified risks.
- Information Security Monitoring and Review: Continuously monitors and reviews the ISMS to ensure its effectiveness and identify areas for improvement.
Navigating the Map: Key Benefits of Implementing ISO 27001
Adopting the ISO 27001 framework offers organizations a multitude of benefits, contributing to improved security posture, operational efficiency, and overall business resilience:
- Enhanced Security Posture: ISO 27001 provides a structured approach to identifying, assessing, and mitigating information security risks, significantly strengthening an organization’s security posture.
- Increased Trust and Confidence: Demonstrating compliance with ISO 27001 builds trust and confidence among stakeholders, including customers, partners, and investors.
- Improved Data Protection: The framework emphasizes data confidentiality, integrity, and availability, ensuring robust data protection measures are in place.
- Reduced Security Incidents: By proactively addressing security risks, organizations can significantly reduce the likelihood and impact of security incidents.
- Enhanced Compliance: ISO 27001 facilitates compliance with various industry-specific and regulatory requirements, reducing the risk of legal and financial penalties.
- Improved Business Continuity: The framework incorporates business continuity management principles, ensuring the organization’s ability to recover from disruptions.
- Competitive Advantage: Demonstrating a commitment to information security through ISO 27001 certification can provide a competitive advantage in the marketplace.
FAQs about ISO 27001
Q: Who should implement ISO 27001?
A: ISO 27001 is applicable to organizations of all sizes and industries, from small businesses to multinational corporations. Any organization that handles sensitive information, whether it be financial data, customer records, or intellectual property, can benefit from implementing this framework.
Q: What is the difference between ISO 27001 and ISO 27002?
A: ISO 27001 outlines the requirements for establishing, implementing, maintaining, and continuously improving an ISMS. ISO 27002, on the other hand, provides a set of practical security controls that can be used to meet the requirements of ISO 27001.
Q: How long does it take to implement ISO 27001?
A: The implementation timeframe varies depending on the size and complexity of the organization, as well as the existing security controls in place. However, a typical implementation process can take anywhere from six months to two years.
Q: What are the costs associated with ISO 27001 implementation?
A: The costs associated with ISO 27001 implementation can vary depending on factors such as the organization’s size, the complexity of its IT infrastructure, and the chosen implementation approach. Costs may include internal resources, external consultants, training, and certification audits.
Q: What are the benefits of getting ISO 27001 certified?
A: ISO 27001 certification provides independent verification that an organization’s ISMS meets the requirements of the standard. This certification demonstrates a commitment to information security, enhances trust among stakeholders, and can provide a competitive advantage.
Tips for Implementing ISO 27001
- Define clear objectives: Establish specific goals and objectives for implementing ISO 27001, ensuring they align with the organization’s overall business strategy.
- Secure leadership buy-in: Gain support from senior management, emphasizing the importance of information security and the benefits of ISO 27001 implementation.
- Conduct a thorough risk assessment: Identify, analyze, and evaluate information security risks, prioritizing those with the highest potential impact.
- Develop a comprehensive security policy: Establish a clear security policy that defines the organization’s commitment to information security and outlines responsibilities.
- Implement appropriate security controls: Select and implement security controls based on the identified risks and the organization’s specific needs.
- Provide training and awareness: Educate employees about information security best practices, their responsibilities, and the potential consequences of security breaches.
- Regularly monitor and review: Continuously monitor and review the ISMS to ensure its effectiveness, identify areas for improvement, and adapt to changing threats and technologies.
Conclusion: Navigating the Path to Information Security Excellence
ISO 27001 provides a comprehensive framework for navigating the complex landscape of information security. By implementing this framework, organizations can strengthen their security posture, build trust among stakeholders, and gain a competitive advantage in the marketplace. While the journey to full compliance may be challenging, the rewards in terms of improved security, operational efficiency, and business resilience are substantial. By embracing the ISO 27001 roadmap, organizations can confidently navigate the ever-evolving world of information security and ensure the protection of their valuable assets.





Closure
Thus, we hope this article has provided valuable insights into Navigating the Landscape of Innovation: A Comprehensive Guide to the ISA Framework. We thank you for taking the time to read this article. See you in our next article!